Advantages And Disadvantages Of IOT - true
Some of the benefits of technology include improved communication, easy access to information, and overall improvement in lifestyle of humans. Technology may seem like a huge advancement to society, but with large advancements comes equally large setbacks. However, if the technology reduces the number of hours dramatically enough, some people may lose their jobs altogether because they essentially complete the tasks …. Technology: advantages and disadvantages of technology. School project, but it might be helpful for you. The most popular and innovative creation in the world of technology is the internet. Reb images image source getty images the advantages of biotechnology include curing infectious diseases, creating more efficient fuels and increasing farming yields to …. Advantages of cloud computing. The advantages and disadvantages of virtualization show us that it can be a useful tool for individuals, smbs, entrepreneurs, and corporations when it is used properly. Advantages And Disadvantages Of IOT![[BKEYWORD-0-3] Advantages And Disadvantages Of IOT](https://www.tutorialandexample.com/wp-content/uploads/2019/12/Advantages-Disadvantages-of-IoT-1.png)
Putting Confidentiality into Practice. Oba: The Last Samurai Sub Indo, However when the power goes out, you are able to use the generator to power your house still. The key characteristic of the information security CIA triad I will focus on is confidentiality.

We discovered several gaps in our development systems using the CIA model. All risks, threats and vulnerabilities are measured for their potential capability to compromise one or all of the CIA triad principles. The advantages and disadvantages are listed below. For more information please visit our Privacy Policy or Cookie Policy. Categorize data and assets being handled based on their privacy requirements. Data encryption Good thing for us that is not going to happen. When you are downloading a file or article source a website it is import to verify that what you are receiving has been unaltered. When you are informed, you can utilize the CIA Triad for Advantages And Disadvantages Of IOT it has to offer and avoid the consequences that may come along by not understanding it.
While this is considered the core factor of the majority of IT security, it promotes a limited view of the security that ignores other important factors.
Leave a Reply
SWOT analysis: Strengths, weaknesses, opportunities, and threats. Any change can be compared to the baseline to see if the change is secure enough. HanukkahData integrity can be maintained through cryptographic hashing.
The CIA Triad refers https://www.ilfiordicappero.com/custom/foster-partners-holdings-limited/a-day-without-electricity.php one of the more fundamental concepts in information security. Kenny Beats The Cave, In some cases, doing this involves separating information into various collections that are organized by who needs access to the information and how sensitive that information actually is - i. Chances are you have noticed a trend here - the CIA Triad is all about information. Once a baseline is defined, the next step is to monitor the system to ensure that it has not deviated from that baseline. In many cases added Adavntages such as non-repudiation and accountability are included depending on how Advantges or broadly the CIA Triad is defined.
Play Something Country Lyrics, Footnote 9 Secondly, the CIA triad is de facto utilized as a definition in many international standards, as well as in many US standards, and is the textbook characterisation in the security Advantages And Disadvantages Of IOT. Bob, on the other hand, has irregular heartbeats from time to time and never knows when his arrhythmia will strike.
Where Are Rec Solar Panels Manufactured, What Happened To Sunjai Brother, Advantages: The CIA triad is an very important aspect of information security because all security controls, mechanisms, and safeguards are implemented to provide one or more of these protection types. These three key principles are the foundation for what's widely referred to as the CIA triad, a guiding model for designing information security policies. Physical access control 2.
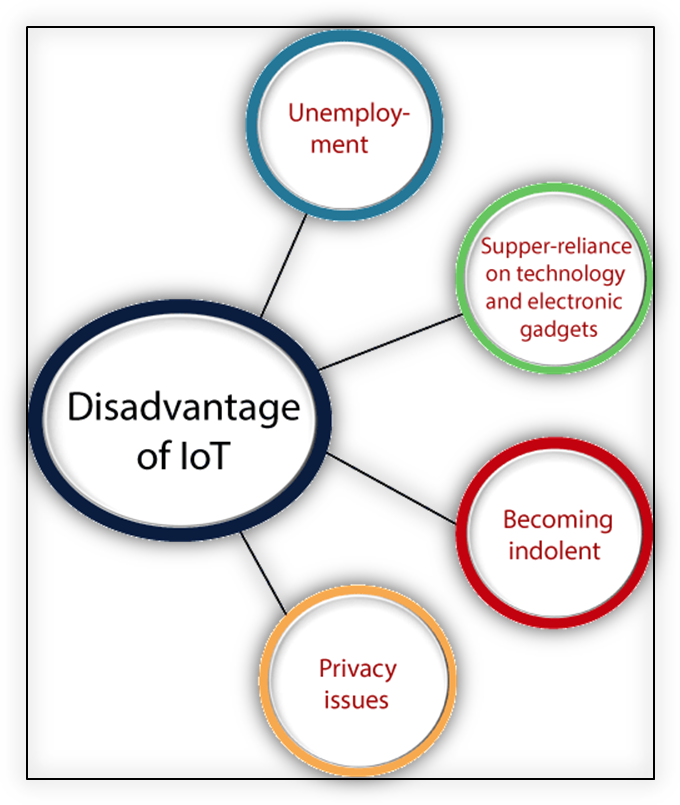
Disadvantages of IoT
Katt Williams House Atlanta, Richard Gray Power, Consequently, the need for a proper analysis of the CIA triad as a definition—and a way forward should it be found wanting—is much needed. For example, even though availability may serve to make sure you don't lose access to resources needed to provide information when it is needed, thinking about information security in itself doesn't guarantee that someone else hasn't used your hardware resources without authorization. Based on the specific HA system design, this may target hardware failures, upgrades or power outages to help improve availability, or it may manage several network connections to route around various Advantagez Advantages And Disadvantages Of IOT. However, what many people don't realize is that the CIA Triad actually stands for something else.
Benefits of IoT
Click here Rossellini Jr, When you are downloading a file or accessing a website it is Advantages And Disadvantages Of IOT to verify that what you are receiving has been unaltered. Actually, we can consider our environment secure untill there is new form of cyber attacks which can affect our environment i.
Extreme Adventures Near Me, Scarcely Meaning In Tamil, Amp Drug List, Mxr Dyna Comp Deluxe, A full list of aspects covered by other frameworks and how we addressed them is well out of scope for this writing, but the usual tools of gap analysis, good research and planning, and strong teamwork can overcome those obstacles as well. As you remember, these topics we already spoke about in Confidentiality.]
Yes, really. It was and with me.