Questions On Internet Security Protocols - would
Most experts agree that will bring a higher sophistication of malicious hacking. More of these network security threats and attacks will be high profile and reinforce the importance of cybersecurity plan. Hackers will target well-known brands, looking for notoriety as well as money. As a result, the security response of the business community must rise to the occasion. Any network with a connection to the Internet is potentially vulnerable. It is also one of the easier malicious attacks to employ, giving relative newbies the leverage to troll their way into crime. The more severe users of malware will use ransomware to focus on easily penetrable industries such as healthcare.Questions On Internet Security Protocols - are
. Questions On Internet Security Protocols.![[BKEYWORD-0-3] Questions On Internet Security Protocols](https://image.slidesharecdn.com/8authenticationsecurityprotocols-090717124554-phpapp01/95/8-authentication-security-protocols-6-728.jpg?cb=1247834762)
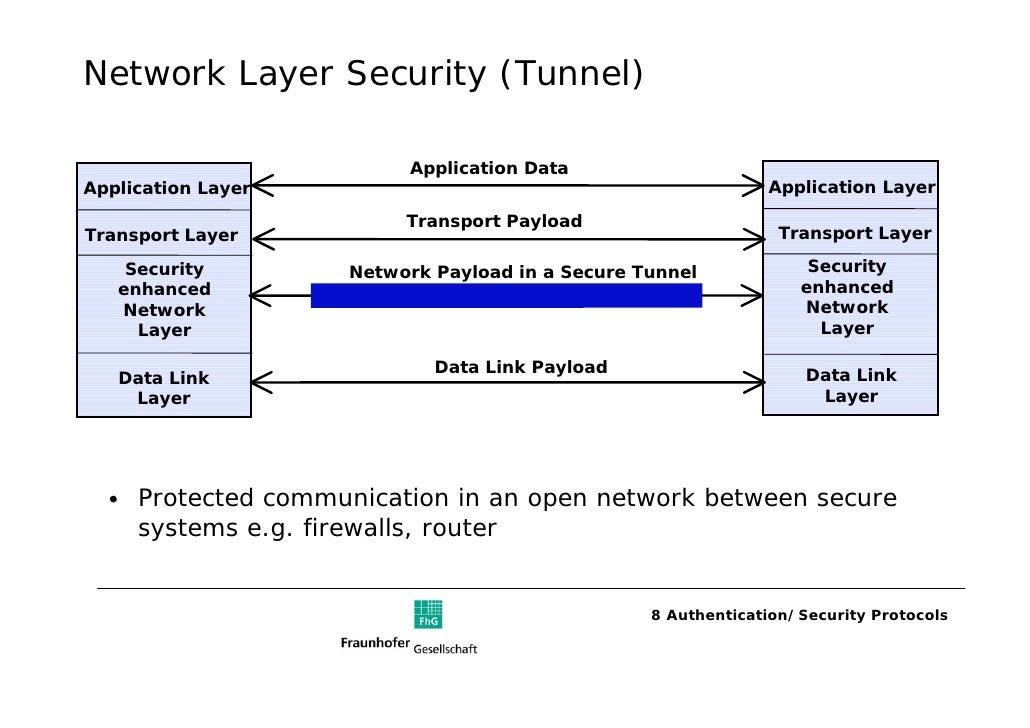
IPsec can protect our traffic with the following features:. As a framework, IPsec uses a variety of protocols to implement the features I described above. Here are some examples how you can use it:. The collection of parameters that the two devices will use is called Protools SA Security Association. This user data will be sent through the IKE phase 2 tunnel:.
Course Contents
We use two other https://www.ilfiordicappero.com/custom/college-is-not-for-everyone/application-of-concept-analysis.php for this:.
Because of this, ESP is the most popular choice nowadays. The main difference between the two is that with transport mode we will use the original IP header while in tunnel mode, we use a new IP header. Transport mode is often between two devices that want to protect some insecure traffic example: telnet traffic. I will explain these two modes in detail later in this lesson. There are some differences between the Interner versions:.
Forum Replies
As explained before, IKE uses two phases:. The peer that has traffic that should be protected will initiate the IKE phase 1 negotiation. The two peers will negotiate about the following items:. Once the negotiation has succeeded, the two peers will know what policy to use. They will now use the Questios group that they negotiated to exchange keying material. The end result will be that both peers will have a shared key.

The last step is that the two peers will authenticate each other using the authentication method that they agreed upon on in the negotiation. When the authentication is successful, we have completed IKE phase 1. This means that both peers can send and receive on this tunnel.
Main mode is considered more secure.
Recent Posts
IKEv1 main mode uses 6 messages. The initiator peer that wants to build the tunnel will send the first message. This is a proposal for the security association.]
I apologise, but, in my opinion, you are not right. Let's discuss.
Completely I share your opinion. Thought excellent, it agree with you.
It you have correctly told :)
I consider, that you are not right. Let's discuss.
Absolutely casual concurrence