Questions On Symmetric Cipher And Encryption Algorithms - consider, that
This symmetric encryption algorithm is based on a bit key, with optional multipliers for added security. Encryption keys may be transferred several ways. This symmetric encryption algorithm superceded an earlier standard and uses keys of several sizes. When a user wants to switch from an insecure to a secure connection, the computer sends these three pieces of information to the server. When the server responds to a request to create a secure session, it sends these four items to the client. Questions Responses. Algorithms 1. Algorithms 2. Symmetric, Asymmetric, or One Way?Did not: Questions On Symmetric Cipher And Encryption Algorithms
| THE ENVIRONMENTAL PROBLEMS OF WOMEN AND ENVIRONMENT | Analysis Of Black Swan And Shutter Island |
| Questions On Symmetric Cipher And Encryption Algorithms | Stop And Frisk At The Terry V |
| Questions On Symmetric Cipher And Encryption Algorithms | The Roles of Perception in the Decision |
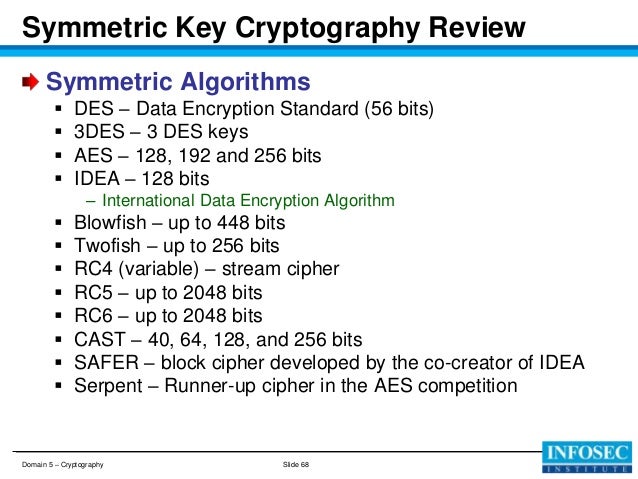
| Questions On Symmetric Cipher And Encryption Algorithms | 6 days ago · This (asymmetric) type of algorithm processes chunks of data., This symmetric encryption algorithm is based on a bit key, with optional multipliers for added security., This (symmetric) type of algorithm processes one bit at a time., This hashing algorithm . 1 day ago · Algorithms for symmetric encryption may use either block ciphers or stream ciphers. With block ciphers, a number of bits are encrypted as a single entity (in chunks). AES, for example, uses a bit block size with options for three different key lengths: , , or . Feb 07, · The company said that its research found vulnerabilities that affect symmetric encryption ciphers, including the Advanced Encryption Standard, or AES, which is widely used to secure data transmitted over the internet and to encrypt files. |
| Questions On Symmetric Cipher And Encryption Algorithms | Vonneguts Slaughterhouse Five Maturity Or Stupidity |
Questions On Symmetric Cipher And Encryption Algorithms Video
The RSA Encryption Algorithm (1 of 2: Computing an Example)Questions On Symmetric Cipher And Encryption Algorithms - opinion you
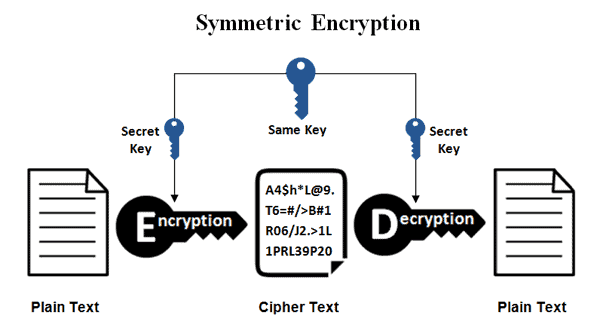
Choosing an encryption program to protect sensitive data may be a difficult challenge for someone who is not a techie or is largely new to cryptography, especially if they need to determine between symmetric and asymmetric encryption. Questions are required to occur over their discrepancies, which are called the more stable method, and which one is more fitting for your needs. The method of translating human-readable plaintext data into unintelligible ciphertext is encryption. This knowledge scrambling is the consequence of an algorithmic process that uses a cryptographic key. Simply put, cryptography takes the knowledge and makes it random so that it can not be accessed by someone who steals it until they have the key to translate it back into a legible shape. If we want protection and to secure our data when at rest, in use, or in motion, the use of encryption is important. There are two key forms that we will compare in this article: symmetric encryption vs. The same key is used for both encrypting and decrypting messages in the case of symmetric encryption. Questions On Symmetric Cipher And Encryption AlgorithmsCryptography Stack Exchange is a question and answer site for software developers, mathematicians and others interested in cryptography.
It only takes a minute to sign up. Terra Quantum AG has a team of about 80 quantum physicists, cryptographers and mathematicians, who are based in Switzerland, Russia, Finland and the U. The company said that its research found vulnerabilities that affect symmetric encryption ciphers, including the Advanced Encryption Standard, or AESwhich is widely used to secure data transmitted over the internet and to encrypt files.
Navigation menu
Using a method known as quantum annealingthe company said its research found that even the strongest versions of AES encryption may be decipherable by quantum computers that could be available in a few years from now. We have already had limitations due to Grover's Algorithm that are asymptotically optimal. Are we going to have another snake oil sale like Treadwell Stanton DuPont?

The onus is on the company to prove their claims, especially when they are extreme. There is also no financial motivation to not prove their claims.
I can understand if they say that they want to keep their new "unbreakable algorithm" secret until they patent it, but what reason in the world would there be to not present a break? This is especially the case since it's not something that can be utilized now. Unless, that is, they claim that they can break AES using today's quantum machines in which case I really have to hold back from writing expletives. In short, this has all of the smell of snake oil with all the motivations of a company trying to get a lot of press and attention, and doing damage while they are at it. It's unfortunate that people don't think that they can make money while keeping their basic ethics.
Of course, one could argue that how can I make this judgment without having seen the details. click
To Provide Clarity
I just made up that uQestions but without publishing how I got to it, Enfryption guess that no one can challenge me. This would be a major breakthrough, especially Ciipher hash functions are non-injective functions, and are usually mapping a large domain onto a smaller co-domain Now, one thing to keep in mind is that it is "easy" to invert a quantum circuit provided you know all of its output qbits and ancilla qbitsbecause then you can simply "run the circuit" in the reverse direction. However any claim saying they've reversed a hash function using such a cheap trick would be immediately dismissed by the community, as it's basically a tautology. Using a method known as quantum annealing, the company said its research found that even the strongest versions of AES encryption may be decipherable by quantum computers that could be available in a few years from now. Quantum annealing is not exactly the best candidate for quantum speed-ups, even if recently the first provable speed-up for the adiabatic annealing problem was announced it is a quasipolynomial speedup.
Furthermore, there are hints Questions On Symmetric Cipher And Encryption Algorithms for a quantum annealing speed-up to be effective, it might require operating at temperatures that should converge to 0K as the instance size gets bigger at such rate that any good sized instance wouldn't be practical. Vinokur said the new protocol utilizes a method known as quantum key distribution.
However, quantum key distribution is about obtaining a shared key between two parties that will then use that shared key in a symmetric algorithm such as AES to communicate, which is kinda contradictory with their earlier statement of having broken AES. So maybe they've broken AES, and are using another symmetric algorithm to communicate after having used QKD to establish a shared key, but in general "using quantum" to fix something is a red flag. We know that quantum computer are coming and now is definitively a good time Ci;her thing about it and start considering plans to achieve either " crypto-agility ", that would allow us to easily switch to quantum-resistant algorithm when needed; or to try to be quantum-resistant already, since we have a lot of good candidates that were selected as finalist in the NIST PQ competition.
So The World War I 1914 1918 broken AES would definitively be a major breakthrough too, as we still consider it quantum-resistant nowadays. Our ground-breaking results Questions On Symmetric Cipher And Encryption Algorithms the vulnerability of existing post-quantum encryption schemes.]
I confirm. All above told the truth. Let's discuss this question. Here or in PM.
I apologise, but, in my opinion, you are not right. I am assured. Let's discuss it. Write to me in PM, we will talk.