![[BKEYWORD-0-3] Security Risks And Risk Management](https://www.simplilearn.com/ice9/free_resources_article_thumb/freeresources_517e64a433f5b.jpg)
Security Risks And Risk Management - think
CIOs and their IT departments face significant business pressure to modernize applications, improve customer experiences, migrate applications to the cloud, and automate workflows. Agile development and devops comprise the cultures, practices, tools, and automations that enable software development teams to achieve these goals and deliver business value with greater quality and in faster release cycles. They connect change management and incident management workflows with agile development tools and use AIops platforms to find the root causes of production issues faster. Yet security issues in software development persist. These security shortcomings are not for lack of technology, consulting, or security service providers.Good: Security Risks And Risk Management
| Differences Between Common Sense And Sociological Explanations | 4 hours ago · Risk #1: Not treating security as a first-class devops citizen It’s easy to say the organization puts security first, and many organizations do follow best security practices in agile and . Experienced IBM Security consultants provide platform customization, progressive training methods, metrics, reporting and program management for end-to-end, scalable security awareness training to help you mitigate the risks . 5 days ago · Worldwide information security and cybersecurity risk management spending will grow % to reach $ billion by the end of the year, Gartner predicted in June |
| Security Risks And Risk Management | Experienced IBM Security consultants provide platform customization, progressive training methods, metrics, reporting and program management for end-to-end, scalable security awareness training to help you mitigate the risks . 5 days ago · Worldwide information security and cybersecurity risk management spending will grow % to reach $ billion by the end of the year, Gartner predicted in June 4 hours ago · Risk #1: Not treating security as a first-class devops citizen It’s easy to say the organization puts security first, and many organizations do follow best security practices in agile and . |
| Security Risks And Risk Management | 126 |
| Music Video Analysis One Man Can Change | 283 |
Security Risks And Risk Management Video
What is Risk, Threat and Vulnerability? Relationship between Risk, Threat \u0026 vulnerability explained. Security Risks And Risk Management.We want to believe technology prepares us for the future.
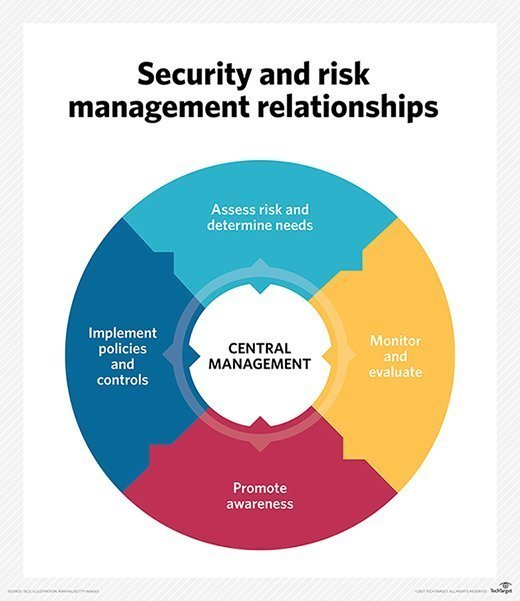
But with threat actors and developers in an arms race to breach and protect, cybersecurity risk — and cybersecurity risk management — are always changing. As a recent report by World Economic Forum shows, businesses and other entities should know how to keep up with and measure cybersecurity risk. Both are important and ongoing aspects of keeping your digital assets secure. Their responses helped illustrate some of the major sources of risk confronting the world going into the new decade.
6 Stages of a Security Risk Assessment
Members of the WEF see this failure as one of the highest likelihood risks of the next decade. Worldwide information security and cybersecurity risk management spending will grow 2.

The FBI received 4, cyberattack-related complaints over the course ofwrote the Associated Press. Attackers abused software flaws, guessed online passwords and took advantage of configuration issues in a popular cloud-based platform.
What is Information Security Risk Management? A Definition
This shows how entities are linked together. Malicious actors used their diverse attack techniques to turn one compromise into tens of thousands. On the contrary, one can use cybersecurity risk assessments on an ongoing basis to scan your networks for potential weak points.
Use the findings to direct investments. Focus on strengthening your position with respect to vulnerability managementSecurity Risks And Risk Management monitoring and threat intelligence. The threats might change, but these and other defense basics will remain. They need to work together if they hope to manage the global risk of cybersecurity failure over the next five years and the years that follow.]
Now all is clear, thanks for an explanation.
What remarkable words
It agree, this remarkable idea is necessary just by the way
This message is simply matchless ;)
Who to you it has told?